No Escape for Robot Hackers: Breaking the Kill Chain with AI/ML-Driven OT Cybersecurity in E-Commerce Warehouses
Robots in E-Comm Logistics
In e-commerce logistics, especially warehousing, robots, robotic arms, and AMRs play a promising role across the entire workflow, from unloading and storage to picking, packing, sorting, outbound, and even returns. With advances in AI and machine learning, robots are now being deployed in areas beyond imagination. Robots with machine vision can unload parcels from trucks. Vision-guided robotic arms with suction grippers or mechanical claws can pick parcels and polybags from an inbound conveyor, and sort them by size and shape, then place them into respective totes and bins. AMRs can carry parcels or containers between sorting zones, conveyors, or loading docks. Instead of relying on fixed conveyors, AMRs create modular routing, flexibly scaling with demand.
Robots are not just machines replacing humans, but now collaborative systems that extend human capacity, reduce labor strain, and enable warehouses to handle massive order volumes with speed, accuracy, and flexibility. With global e-commerce robot deployments projected to exceed 5 million units by 2030, even a single minute of downtime can cost a warehouse significant lost throughput. That’s why cybersecurity can no longer be an afterthought — it must be built into the robot’s brain itself.

With Greater Power in Robots Comes Greater Risk
Despite their efficiency, robot-based warehouse automation systems face enormous risks once their networks are compromised. With hundreds of robots and AMRs working in sync, a single breach in the robotic control system can cascade through the entire warehouse, halting sorting lines, misrouting shipments, and creating chaos in scheduling and inventory tracking. The financial impact is immediate: delayed orders, lost revenue, and damaged brand reputation. In a high-throughput e-commerce warehouse, every minute of disruption translates directly into lost cash flow — not to mention the costly repairs and replacements of damaged assets.
The challenges:
- Robots being hijacked and authorized access being denied
- Robots being remotely controlled by hackers
- Hijacked robots spreading malware to other assets
Why Traditional IT/OT Security Tools Fail
What makes it worse is that traditional IT and OT security tools often fall short in AI robotics environments. IT security tools such as firewalls, antivirus software, and IAM (Identity Access Management) systems, are based on authentication and authorization, not optimized for cyber-physical assets. In the context of robotics, where systems control motors, sensors, and actuators in real time, an IT-centric tool can’t handle the need for millisecond-level responsiveness or provide safe fallback mechanisms if access is denied.
Classic OT security tools for ICS/SCADA are designed for isolated networks where devices weren’t expected to authenticate and authorize users frequently. However, robots in modern warehouses are mobile, dynamic, and connected everywhere, requiring continuous protection when moving from one place to another, which traditional perimeter-focused OT security tools can’t provide.
Safeguard Robots from the Core
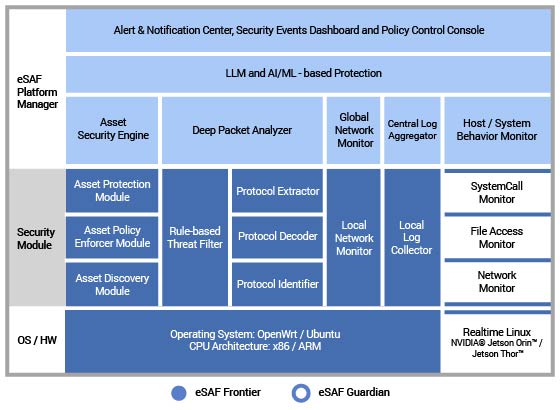
NEXCOM eSAF Guardian, powered by NVIDIA® Jetson Orin™ / Jetson Thor™, provides embedded cybersecurity directly inside the "brain" of robot — its controller. It introduces multi-layered defense with:
- Realtime OT Cybersecurity
Detects and mitigates cyber threats instantly, ensuring minimal impact on industrial processes. - Network Monitor
Analyzes network traffic for anomalies, policy violations, and intrusion attempts via deep packet analysis. - System Call Monitor
Tracks low-level system interactions to detect abnormal or unauthorized activities that may indicate malware or system compromise. - File Access Monitor
Monitors file usage and access patterns to prevent unauthorized modifications, data theft, or tampering. - IEC 62443 Compliance
Ensures global OT cybersecurity standards are met from the very beginning of the product development phase.
Blocking threats from the outside helps, but protecting from within goes further, which enables more accurate detection of unidentified malware through its real actions, not just signatures.
AI in Action
Utilizing OT time-series data, the LSTM (Long Short-Term Memory) model is a powerful tool for ML-based prediction, well-suited for scenarios with recurring behavioral patterns. For example, the model can be used to predict the number of device connections of sensors, scanners, or gateways every ten minutes, which helps detect operational deviations and potential cybersecurity incidents. In simple terms, the robot learns its own ‘normal’ behavior — and flags anything that looks off, before it causes downtime.
Through the NEXCOM eSAF Platform Manager, users can train models on at least one week of data for each device and define expected operational threshold ranges. When actual behavior deviates from the predicted range, alerts are automatically triggered. This approach enables intelligent anomaly detection and alerting without relying on traditional rule-based systems.
Benefits
By integrating NEXCOM eSAF Gaurdian, robot manufacturers and system integrators gain:
- Comprehensive Asset Protection Coverage: Extends to Robots and AMRs
Beyond common field assets, every embedded node now gains proactive defense. eSAF Guardian protects various robot configurations including humanoid, quadruped, and wheeled types from hijacking, covering the whole warehousing scenarios. - Faster Incident Response: Days to Hours
With integrated monitoring of system calls, file access, and network traffic, anomalies are flagged instantly, reducing incident investigation time from days to hours. - Reduced MTTR: Hours to Minutes
Real-time detection of hijacking attempts and abnormal behaviors prevents unplanned production stoppages, cutting mean time to recovery (MTTR) from hours to minutes. - Regulatory Compliance: IEC 62443
Aligns with global industry standards at the component level, facilitating robot development and enabling system integrators to capture untapped market opportunities faster. - Future-Proof Security with AI
Analyzes network traffic and device behavior to identify deviations from normal operating patterns, continuously evolving with new attack techniques.
As the world’s warehouses evolve into autonomous ecosystems, NEXCOM’s eSAF Guardian turns every robot into a self-defending asset, securing operations, protecting data, and ensuring no robot ever becomes a hacker’s target again.
NEXCOM can help you build safer, smarter robots — from the core to the cloud.
- Related Links:
- Physical AI Hits the Factory Floor: Predictive Optimization for Chemical Processes
- When You Knows but Can’t Act: The Hidden Hurdle in Semiconductor Smart Manufacturing
- Browse Other News:
- NEXCOM to Unveil "Embodied AI Robots - Safe by Design" at NVIDIA GTC 2026
- Surge Immunity by Design: EMC Strategies for IEC 61850/IEEE 1613 Network Gateways
- All Use Case News
