eSAF OT Security Solution
TMR Technologies Co., Ltd. (TMRTEK), a subsidiary of NEXCOM, specializes in the development of cybersecurity solutions tailored for Operational Technology (OT), Industrial Control Systems (ICS), and the Industrial Internet of Things (IIoT). Our cutting-edge platform, eSAF, stands as TMR's dedicated OT cybersecurity protection solution, encompassing a wide array of functionalities.
These functionalities include monitoring of on-site devices, data gathering, packet filtering, threat identification, proactive threat prevention, device and system protection, monitoring of threat indicators, analysis of potential risks and vulnerabilities, and the provision of effective threat countermeasures.
The eSAF Frontier X/V series is meticulously crafted to safeguard valuable assets, while the eSAF Platform Manager is deployed for the comprehensive protection of OT systems. These solutions find application in critical infrastructures such as manufacturing plants, petrochemical facilities, energy sectors (oil, natural gas, power), and water resources. By doing so, they ensure the uninterrupted operation of systems and serve as the ultimate line of defense for critical equipment.
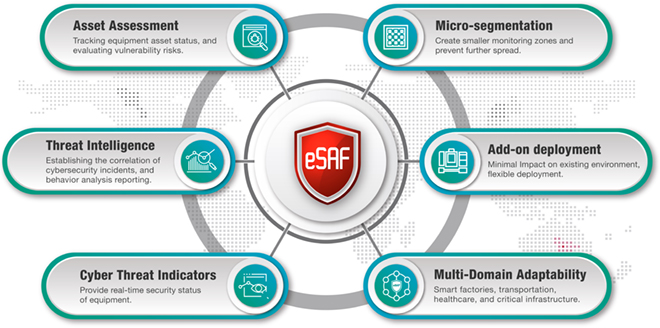
Threats Scenarios |
Vulnerabilities Scenarios |
|
|
Protection Coverage
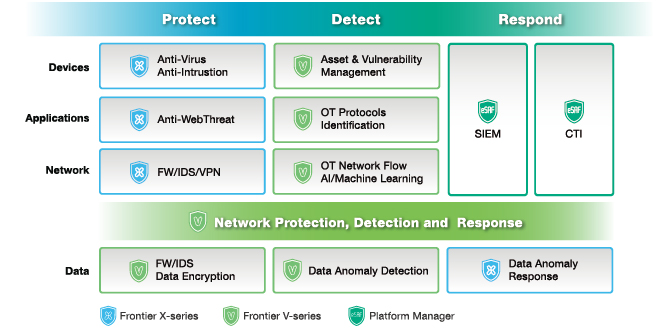
Solution Scope
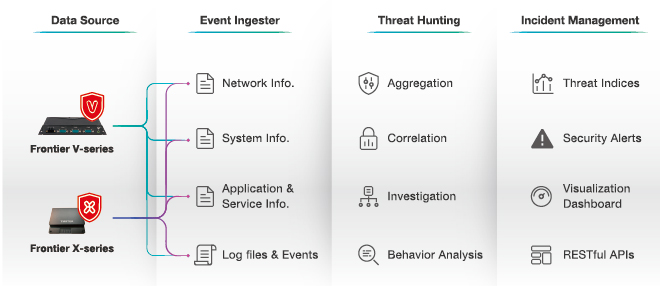
System Architecture
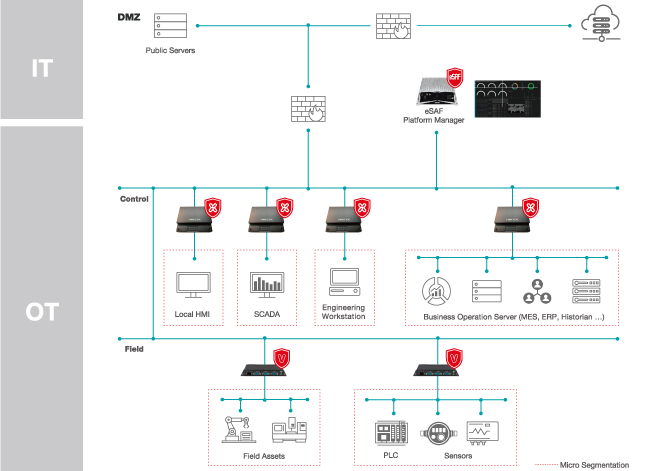
Offering Portfolio

Major Functions and Capabilities
Real-Time Threat Detection and Analysis |
Network Security Monitoring |
|
|
Security Dashboard |
Data Integration and Analysis |
|
|
Asset Information Collection |
Machine Learning and Artificial Intelligence (AI) |
|
|
- Related Products
- eSAF Platform Manager Plant Edition
